As you navigate the vast expanse of the internet, your network is constantly under threat from malicious actors seeking to breach your defenses. But fear not, for you’re about to unlock the secrets of a powerful tool in your arsenal: the firewall. In this comprehensive guide, we’ll research into the world of firewalls, dispelling myths and misconceptions along the way. You’ll learn how firewalls work, the different types available, and how to configure them to safeguard your network from even the most sophisticated threats. By the end of this journey, you’ll be well-equipped to fortify your digital stronghold and protect your valuable assets from harm. Before we delve into the details, let’s start with a quick knowledge check to see what you already know about firewalls.
Firewall Knowledge Check Quiz
- Firewall Rule Configuration Simulator: Create a simple interactive tool where readers can practice configuring firewall rules. They could be presented with a scenario and asked to set up appropriate rules to secure a network.
- Drag-and-Drop Network Diagram: Develop an interactive diagram where readers can drag and drop firewall components to create a secure network architecture.
- Interactive Firewall Decision Tree: Create a flowchart-style interactive element where readers answer questions about their network needs, and the tool suggests appropriate firewall solutions.
- Threat Scenario Challenge: Present readers with different network attack scenarios and ask them to choose the best firewall features or configurations to mitigate each threat.
- Firewall Performance Calculator: Develop a tool where readers can input network parameters (like traffic volume, number of connections) and see how different firewall configurations might perform.
- Timeline of Firewall Evolution: Create an interactive timeline where readers can click on different points to learn about key developments in firewall technology.
Great job on completing the quiz! Now that you’ve tested your initial knowledge, let’s start with the basics and build a solid foundation for understanding firewalls.
Definition of a Firewall
The concept of a firewall is often shrouded in mystery, but it’s imperative to understand what a firewall is and how it works to ensure your network security.
Brief Overview
By now, you’ve likely heard of firewalls, but do you know what they do? In simple terms, a firewall is a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predetermined security rules.
Technical Definition
Technically speaking, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules, blocking or allowing traffic to pass through.
At its core, a firewall acts as a gatekeeper, examining each packet of data transmitted between your network and the internet. It analyzes the source, destination, and type of traffic, comparing it to your predefined security rules. If the traffic meets the criteria, the firewall allows it to pass through; otherwise, it blocks the traffic, protecting your network from potential threats.
Brief History and Evolution of Firewalls
You may not realize it, but firewalls have been around for decades, playing a vital role in protecting networks from unauthorized access and malicious activities. To appreciate the significance of firewalls in modern network security, it’s important to understand their origins and evolution over time.
Early Beginnings
Beside the early computer systems, the concept of firewalls emerged in the 1980s as a response to the growing need for network security. The first firewalls were simple routers configured to filter incoming traffic based on predetermined rules. These early firewalls were primarily used by government agencies and large corporations to safeguard their networks from external threats.
Major Milestones
Against the backdrop of rapidly advancing technology and escalating cyber threats, firewalls continued to evolve, with significant milestones marking their development. The introduction of packet filtering, stateful inspection, and network address translation (NAT) transformed firewalls into robust security solutions.
For instance, the 1990s saw the emergence of commercial firewall products, such as DEC SEAL and SunScreen, which offered more sophisticated security features and user-friendly interfaces. This marked a significant shift towards making firewalls more accessible and manageable for organizations of all sizes. As the internet expanded and cyber threats became more complex, firewalls adapted to counter these challenges, incorporating advanced features like intrusion detection and prevention systems (IDPS) and virtual private networks (VPNs).
Types of Firewalls
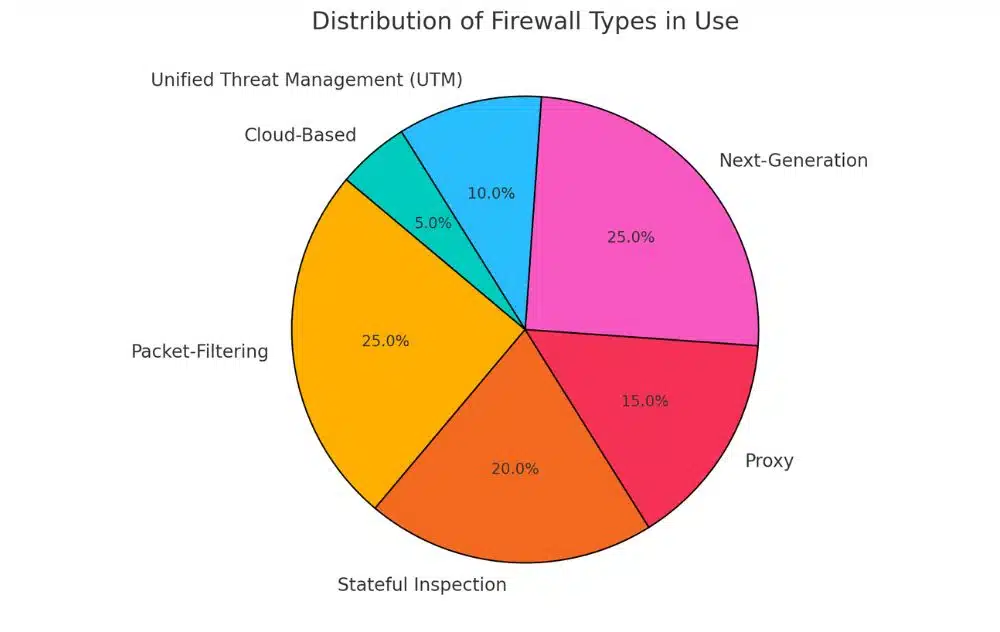
Some of the most common types of firewalls include:
- Packet Filtering Firewalls
- Stateful Inspection Firewalls
- Application Layer Firewalls
- Next-Generation Firewalls (NGFW)
- Cloud Firewalls
- Hardware vs. Software Firewalls
The following table provides a brief overview of each type:
| Firewall Type | Description |
| Packet Filtering Firewalls | Examines packets based on source and destination IP addresses, ports, and protocols |
| Stateful Inspection Firewalls | Tracks the state of network connections, ensuring that incoming packets are part of an existing connection |
| Application Layer Firewalls | Examines traffic at the application layer, providing granular control over specific applications and services |
| Next-Generation Firewalls (NGFW) | Combines traditional firewall capabilities with advanced features like intrusion prevention and malware protection |
| Cloud Firewalls | Provides firewall protection for cloud-based infrastructure and applications |
Packet Filtering Firewalls
For basic network security, packet filtering firewalls are a good starting point. They examine packets based on source and destination IP addresses, ports, and protocols, allowing or blocking traffic accordingly.
Stateful Inspection Firewalls
Inspection of network traffic is taken to the next level with stateful inspection firewalls. These firewalls track the state of network connections, ensuring that incoming packets are part of an existing connection.
A key benefit of stateful inspection firewalls is their ability to prevent unauthorized access to your network. By tracking the state of connections, they can detect and block malicious traffic that might try to exploit open ports or connections.
Application Layer Firewalls
Firewalls operating at the application layer provide granular control over specific applications and services. This allows you to restrict access to certain applications or services, while still allowing legitimate traffic to flow through. When choosing an application layer firewall, consider the specific needs of your organization and the applications you need to protect.
The ability to control traffic at the application layer provides an additional layer of security, as it allows you to block malicious traffic that might be hiding within legitimate applications.
Next-Generation Firewalls (NGFW)
Firewalls have evolved to include advanced features like intrusion prevention and malware protection, giving rise to next-generation firewalls (NGFW). These firewalls combine traditional firewall capabilities with these advanced features to provide comprehensive security.
Stateful inspection and application layer filtering are just a few of the features that make NGFWs so effective. Additionally, they often include features like sandboxing and anti-malware protection to further enhance security.
Cloud Firewalls
Firewalls are no longer limited to on-premises infrastructure; cloud firewalls provide protection for cloud-based infrastructure and applications. When moving to the cloud, consider implementing a cloud firewall to ensure your cloud-based resources are protected.
Cloud firewalls provide the same level of protection as traditional firewalls, but are specifically designed to work with cloud-based infrastructure and applications.
Hardware vs. Software Firewalls
Between hardware and software firewalls, you have two options for implementing firewall protection. Hardware firewalls are physical devices, while software firewalls are installed on individual devices or servers. When deciding between hardware and software firewalls, consider the size and complexity of your network, as well as your budget.
At the heart of the decision is the trade-off between cost and performance. Hardware firewalls are generally more expensive, but provide better performance and scalability. Software firewalls, on the other hand, are more affordable, but may impact system performance.
How Firewalls Work
Many people think of firewalls as a mysterious entity that protects their network from unknown threats. But, in reality, firewalls are simply a set of rules and configurations that control incoming and outgoing network traffic. It’s vital to understand how firewalls work to make informed decisions about your network security.
Basic Principles of Operation
Principally, firewalls operate on a simple principle: they monitor and control incoming and outgoing network traffic based on predetermined security rules. They act as a barrier between your internal network and the external world, ensuring that only authorized traffic passes through. You must configure your firewall correctly to ensure effective security.
Packet Inspection Process
Operationally, firewalls inspect packets of data transmitted between networks, examining their source, destination, and content. They then decide whether to allow or block the packet based on your configured rules. You need to understand packet inspection to appreciate the complexity of firewall security.
Firewalls use various techniques to inspect packets, including stateful inspection, which examines the entire conversation between devices, and stateless inspection, which looks at individual packets. This process happens rapidly, often in a matter of milliseconds, ensuring that legitimate traffic flows smoothly while malicious traffic is blocked.
Rule-Based Filtering
Against the backdrop of packet inspection, firewalls apply rule-based filtering to determine whether to allow or block traffic. You create rules based on factors like source and destination IP addresses, ports, protocols, and packet contents. You must carefully craft your rules to avoid unintended consequences.
At its core, rule-based filtering is a decision-making process. Firewalls evaluate each packet against your rules, allowing or blocking traffic accordingly. This process is both flexible and powerful, enabling you to tailor your firewall configuration to your specific security needs.
Network Address Translation (NAT)
By design, firewalls can also perform Network Address Translation (NAT), which enables multiple devices on a private network to share a single public IP address. You should consider NAT when designing your network architecture.
For instance, when you access a website, your device sends a request to the firewall, which then translates your private IP address to a public IP address. The website responds to the public IP address, and the firewall translates it back to your private IP address. This process happens seamlessly, allowing you to access the internet while keeping your internal network private.
Key Features and Functions
After understanding the basics of firewalls, it’s necessary to explore into their key features and functions. These features are what make firewalls an indispensable component of your network security infrastructure. Here are some of the most important ones:
- Access Control
- Logging and Monitoring
- Intrusion Detection and Prevention
- Virtual Private Network (VPN) Support
- Application Awareness and Control
This comprehensive list of features ensures that your firewall provides robust protection against various types of threats and unauthorized access.
Access Control
For your network to remain secure, you need to control who has access to it. Firewalls provide access control features that allow you to define rules for incoming and outgoing traffic, ensuring that only authorized users and devices can access your network. Make sure to regularly review and update your access control rules to ensure they align with your organization’s security policies.
Logging and Monitoring
Between detecting potential security threats and responding to them, logging and monitoring play a vital role. Firewalls provide logging and monitoring capabilities that enable you to track network activity, identify suspicious behavior, and respond promptly to security incidents.
Considering the vast amount of data generated by network activity, logging and monitoring features help you to identify patterns, trends, and anomalies that may indicate a security breach. This allows you to take proactive measures to prevent attacks and minimize damage.
Intrusion Detection and Prevention
For your network to remain secure, you need to detect and prevent intrusions in real-time. Firewalls equipped with intrusion detection and prevention systems (IDPS) can identify and block malicious traffic, including hacking attempts, malware, and other types of attacks.
Further, IDPS can also alert you to potential security threats, enabling you to take swift action to prevent breaches and minimize damage. This feature is especially important for organizations that handle sensitive data or operate in high-risk environments.
Virtual Private Network (VPN) Support
Control over VPN connections is necessary for securing remote access to your network. Firewalls that support VPNs enable you to create secure, encrypted connections between remote users and your network, ensuring that data remains protected even when transmitted over public networks. Choose a firewall that supports multiple VPN protocols to ensure compatibility with your organization’s VPN infrastructure.
Due to the increasing number of remote workers and mobile devices, VPN support is becoming a critical feature in firewalls. By supporting VPNs, firewalls can extend your network’s security perimeter to remote locations, ensuring that data remains protected regardless of where it’s accessed from.
Application Awareness and Control
To ensure that your network remains secure, you need to control which applications can access it. Firewalls with application awareness and control features can identify and regulate traffic based on specific applications, ensuring that only authorized apps can communicate with your network. Make sure to regularly update your application control rules to ensure they align with your organization’s changing application landscape.
Consequently, application awareness and control features enable you to enforce granular security policies, reducing the risk of attacks and minimizing the attack surface. By controlling which applications can access your network, you can prevent unauthorized access and protect your data from malicious actors.
Firewall Deployment
Unlike other security measures, firewall deployment requires careful planning and consideration to ensure effective network protection.
Network Placement Strategies
Strategically placing your firewall within your network is vital to its success. You’ll need to decide where to position your firewall to maximize its impact, taking into account factors such as network segmentation, traffic flow, and potential attack vectors It’s important to consider the 80/20 rule, where 80% of your security efforts should focus on 20% of your most critical assets.
DMZ (Demilitarized Zone) Configuration
On the periphery of your network, a DMZ serves as a buffer zone between your internal network and the public internet. You can configure your DMZ to host public-facing services, such as web servers, while keeping your internal network isolated.
And, by segregating your DMZ from your internal network, you can limit the attack surface in case of a breach. This adds an extra layer of protection to your network, ensuring that even if an attacker gains access to your DMZ, they won’t be able to directly access your internal resources.
Firewall Chaining
Placement of multiple firewalls in a series, or firewall chaining, allows you to create a layered defense system. You can configure each firewall to perform specific tasks, such as filtering traffic or performing intrusion detection When implementing firewall chaining, it’s important to ensure that each firewall is configured to complement the others, rather than creating redundant or conflicting rules.
Hence, by combining multiple firewalls, you can create a robust security posture that addresses various threats and vulnerabilities. This approach also enables you to distribute the workload among multiple firewalls, reducing the load on individual devices and improving overall network performance When designing your firewall chain, consider the order in which traffic will flow through each device, ensuring that the most critical security checks are performed first.
Firewall Configuration and Management
Once again, as you research deeper into the world of firewalls, you’ll encounter the need to configure and manage your firewall effectively. This chapter will guide you through the process of creating and managing firewall rules, best practices for rule organization, performance tuning, and optimization, as well as updating and patching your firewall.
Creating and Managing Firewall Rules
By defining rules, you’re vitally telling your firewall what traffic to allow or block. Creating and managing these rules involves specifying the source and destination IP addresses, ports, protocols, and actions to take for each rule. This process requires careful consideration to ensure that your firewall is secure yet allows legitimate traffic to pass through.
Best Practices for Rule Organization
An vital aspect of firewall management is organizing your rules in a logical and structured manner. This includes grouping similar rules together, using clear and descriptive names, and implementing a consistent naming convention.
For instance, you can create separate groups for inbound and outbound traffic, or categorize rules by service or protocol. This organization makes it easier to manage and maintain your rules, reducing the risk of errors or oversights.
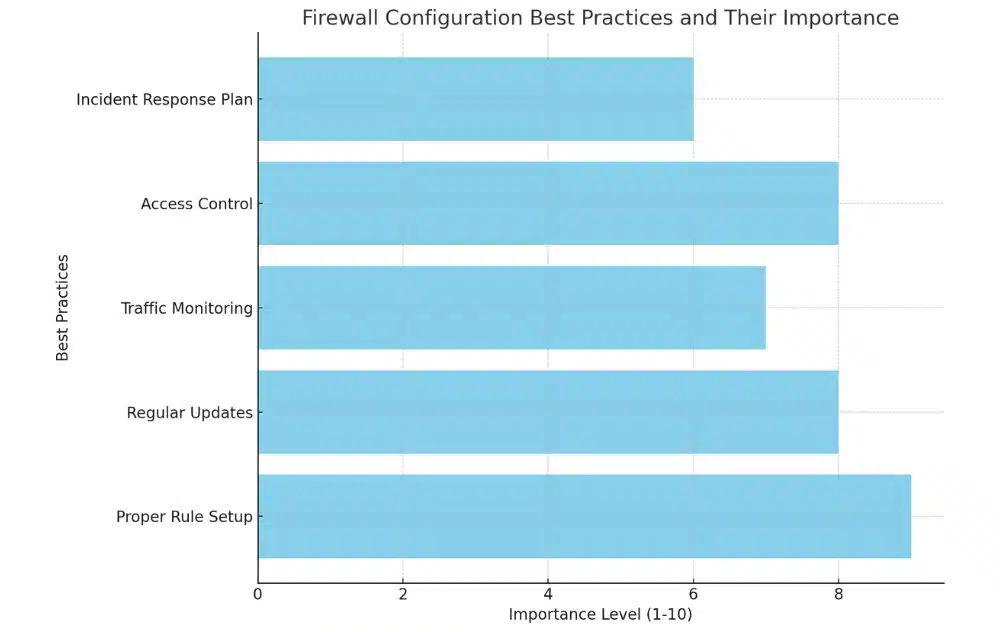
Best Practices for Firewall Configuration
To ensure a firewall operates effectively, certain configuration practices are essential. These include:
- Setting up proper rules
- Regularly updating the firewall
- Monitoring network traffic
- Implementing access control
- Establishing an incident response plan
The following chart highlights the relative importance of each best practice:
Performance Tuning and Optimization
After configuring your firewall rules, you’ll want to ensure that your firewall is performing optimally. This involves monitoring system resources, adjusting settings for improved throughput, and fine-tuning your rules to minimize latency and maximize security.
Management of your firewall’s performance is critical to maintaining a secure and efficient network. You’ll need to regularly review system logs, adjust settings as needed, and consider upgrading hardware or software to keep pace with growing network demands.
Updating and Patching
Tuning your firewall’s software and firmware is vital to staying ahead of emerging threats. Regular updates and patches provide new features, fix vulnerabilities, and improve performance. Failing to update your firewall can leave your network exposed to known vulnerabilities.
Due to the ever-evolving nature of cyber threats, it’s vital to stay vigilant and proactive in updating and patching your firewall. This includes setting up a regular schedule for updates, monitoring vendor releases, and testing patches before deployment to ensure minimal disruption to your network.
Firewall Security
Despite the importance of firewalls in protecting your network, many individuals and organizations fail to properly configure and maintain them, leaving their systems vulnerable to attacks. As you can learn more about in Understanding Firewalls: Your Essential Guide to Network Security, a well-configured firewall is imperative to preventing unauthorized access to your network.
Common Firewall Vulnerabilities
Behind every robust firewall lies a set of potential vulnerabilities waiting to be exploited. You should be aware of common weaknesses such as misconfigured rules, outdated firmware, and inadequate logging and monitoring. It’s imperative to stay up-to-date with the latest security patches and updates to prevent exploitation.
Hardening Techniques
One of the most effective ways to strengthen your firewall is by implementing hardening techniques. This includes disabling unnecessary services, restricting access to specific IP addresses, and configuring intrusion detection and prevention systems.
Hence, hardening your firewall involves a combination of technical expertise and careful planning. By following best practices and staying informed about emerging threats, you can significantly reduce the risk of a security breach.
Regular Security Audits and Assessments
To ensure your firewall remains effective, it’s imperative to conduct regular security audits and assessments. This involves testing your firewall’s configuration, identifying vulnerabilities, and implementing necessary changes. Regular audits can help you identify potential weaknesses before they’re exploited by attackers.
Regular security audits also provide an opportunity to review your firewall’s logs, identifying patterns and anomalies that may indicate a potential threat. By staying proactive, you can respond quickly to emerging threats and prevent costly security breaches. Don’t wait until it’s too late – schedule regular audits to ensure your firewall remains a robust defense against cyber threats.
Firewalls in Different Environments
Keep in mind that firewalls are not a one-size-fits-all solution. Depending on the environment, different types of firewalls are needed to provide adequate security.
Enterprise Network Firewalls
Different enterprise networks require robust firewalls that can handle high volumes of traffic and protect against sophisticated threats. When choosing an enterprise firewall, consider scalability and customization options. You’ll want a firewall that can integrate with your existing security infrastructure and provide advanced features like intrusion detection and prevention.
Small Business and Home Network Firewalls
Along with the growing number of connected devices, small businesses and home networks need firewalls that are easy to set up and manage. You’ll want a firewall that provides basic security features like packet filtering and network address translation (NAT).
At the same time, small businesses and home networks often have limited IT resources, so it’s vital to choose a firewall that is user-friendly and doesn’t require extensive technical expertise.
Cloud-Based Firewalls
Beside traditional on-premise firewalls, cloud-based firewalls are becoming increasingly popular. You’ll want a cloud-based firewall that provides scalability, flexibility, and cost-effectiveness, as well as advanced security features like threat intelligence and analytics.
Home in on the benefits of cloud-based firewalls, such as reduced maintenance and updates, and the ability to secure multiple locations and cloud-based applications from a single platform.
Mobile Device Firewalls
One of the most significant challenges in mobile device security is protecting against threats on-the-go. You’ll want a mobile device firewall that provides real-time threat protection, data encryption, and secure browsing capabilities.
Firewalls on mobile devices need to be lightweight, yet powerful, to ensure that your device remains secure without compromising performance.
Integration with Other Security Tools
All firewalls can integrate with other security tools to provide a robust security posture. This integration enables you to leverage the strengths of each tool to protect your network from various threats.
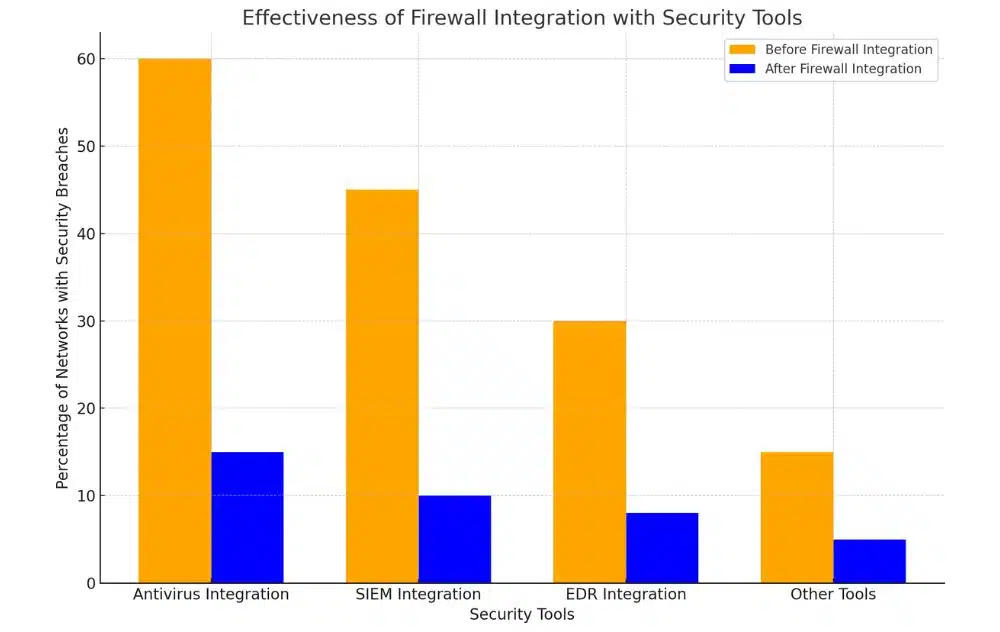
Antivirus and Anti-Malware Integration
Other security tools, such as antivirus and anti-malware software, can work in tandem with your firewall to detect and block malicious code. This integration ensures that your network is protected from both network-based and host-based threats. When choosing an antivirus solution, consider one that can integrate with your firewall to provide comprehensive protection.
Security Information and Event Management (SIEM) Integration
Before deploying a SIEM system, ensure it can integrate with your firewall to collect and analyze log data. This integration provides you with a centralized platform to monitor and respond to security incidents. When choosing a SIEM solution, consider its ability to integrate with your firewall and other security tools.
Management of security event logs is a critical aspect of network security. SIEM integration with your firewall enables you to collect, monitor, and analyze log data in real-time, allowing you to respond quickly to security incidents. This integration also helps you to identify potential security gaps and improve your incident response plan.
Endpoint Detection and Response (EDR) Integration
Information from EDR solutions can be used to enhance your firewall rules and improve threat detection. This integration enables you to respond quickly to endpoint threats and prevent lateral movement within your network.
And, with EDR integration, you can gain visibility into endpoint activity, allowing you to identify and respond to threats that may have evaded your firewall. This integration also enables you to implement a proactive approach to security, rather than simply reacting to threats as they arise.
Firewall Limitations and Bypass Techniques
For every security measure, there’s a potential weakness or limitation. Firewalls are no exception.
Known Limitations of Firewalls
Above all, firewalls are only as good as their configuration and maintenance. If not properly set up or updated, firewalls can become ineffective against sophisticated attacks. Additionally, firewalls may not be able to detect certain types of malware or unauthorized access if they’re not equipped with advanced features like intrusion detection and prevention systems.
Common Firewall Evasion Techniques
Bypassing firewalls has become an art form for hackers. They use techniques like packet fragmentation, IP spoofing, and DNS tunneling to evade detection. It’s crucial to stay informed about these techniques to ensure your firewall is configured to counter them.
Techniques like these are constantly evolving, and it’s up to you to stay ahead of the game. For instance, DNS tunneling involves using DNS queries to transmit malicious data, which can be difficult to detect without advanced security measures in place. By understanding these techniques, you can better configure your firewall to prevent such attacks.
Emerging Threats and Challenges
Firewall technology is constantly playing catch-up with emerging threats like IoT-based attacks, cloud-based attacks, and encrypted malware. As your network evolves, so must your firewall configuration to address these new challenges.
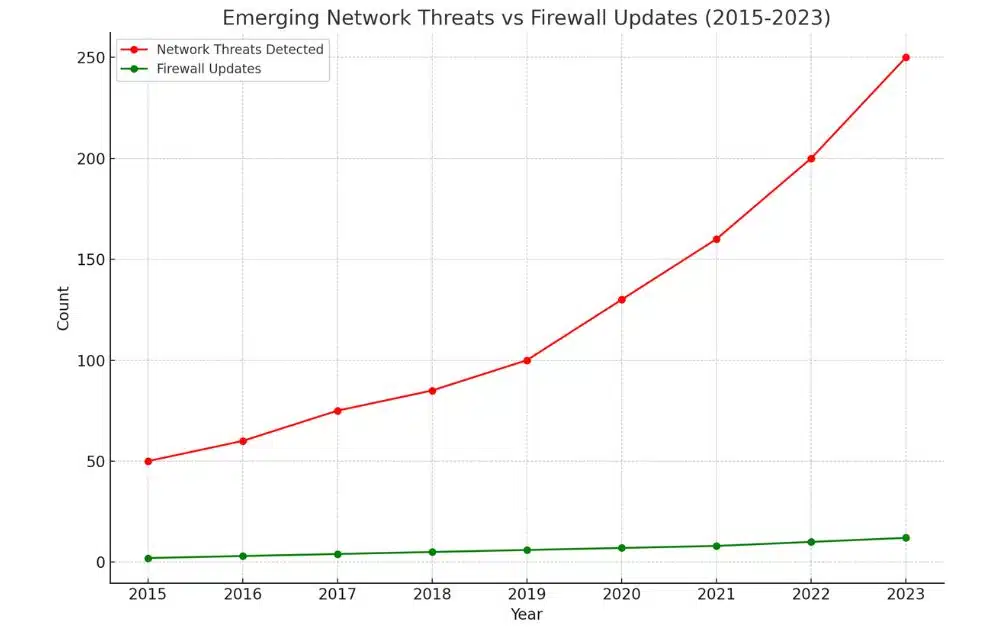
To effectively counter these emerging threats, you need to stay informed about the latest developments in firewall technology and network security. This includes implementing advanced features like next-generation firewalls, which can detect and prevent unknown threats. By doing so, you can ensure your network remains secure in the face of evolving threats.
The Future of Firewalls
Now that you have a solid understanding of firewalls and their role in network security, it’s time to look ahead to the future. The landscape of cybersecurity is constantly evolving, and firewalls must adapt to stay effective.
AI and Machine Learning in Firewall Technology
To improve detection and response capabilities, firewall technology is incorporating artificial intelligence (AI) and machine learning (ML) algorithms. These advancements enable firewalls to analyze vast amounts of data, identify patterns, and make informed decisions about traffic filtering and threat mitigation.
Zero Trust Security Model and Firewalls
With the rise of cloud computing and remote work, the traditional perimeter-based security approach is no longer sufficient. It’s important to adopt a zero-trust model, where all traffic is treated as untrusted, regardless of its source. This shift requires firewalls to evolve and integrate with zero-trust principles, ensuring that access is granted only on a need-to-know basis.
Model your firewall configuration to align with the zero-trust security model, where each request is verified and authenticated before access is granted. This approach helps prevent lateral movement in case of a breach, reducing the attack surface and protecting your network from unauthorized access. Implementing zero-trust principles will become a standard practice in the near future, so it’s important to start planning now.
Adaptive and Intent-Based Firewalls
Between the increasing complexity of threats and the growing demand for network agility, firewalls must become more adaptive and intent-based. This means they should be able to dynamically adjust policies and configurations based on real-time threat intelligence and your organization’s specific security needs.
Security policies will need to be more granular and flexible, allowing firewalls to respond to changing circumstances and prioritize traffic based on business intent. As your network evolves, your firewall should be able to adapt and learn from your environment, ensuring that security keeps pace with innovation. By adopting adaptive and intent-based firewalls, you’ll be better equipped to stay ahead of emerging threats and protect your network from the unknown.
Choosing the Right Firewall
To ensure the security of your network, selecting the right firewall is a vital decision. It’s crucial to consider various factors, weigh the pros and cons of different solutions, and evaluate the total cost of ownership.
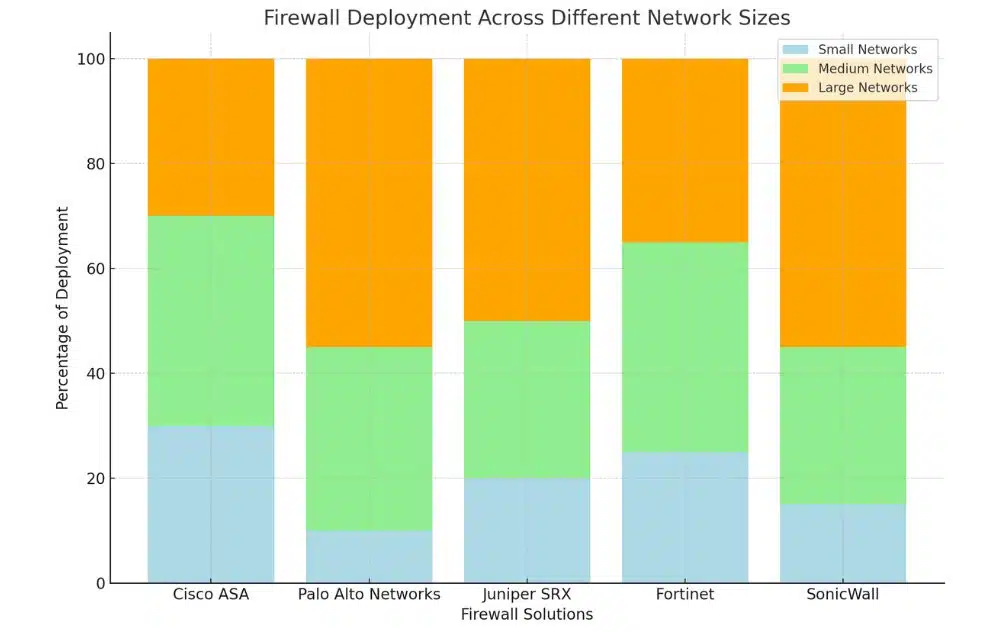
Factors to Consider When Selecting a Firewall
To make an informed decision, you need to consider the following factors: It’s a critical decision that will impact your network’s security posture.
- Network size and complexity
- Type of traffic and applications used
- Security features and functionalities required
- Scalability and flexibility
- Integration with existing infrastructure
- Cost and budget constraints
- Thou shalt also consider the level of support and maintenance provided by the vendor.
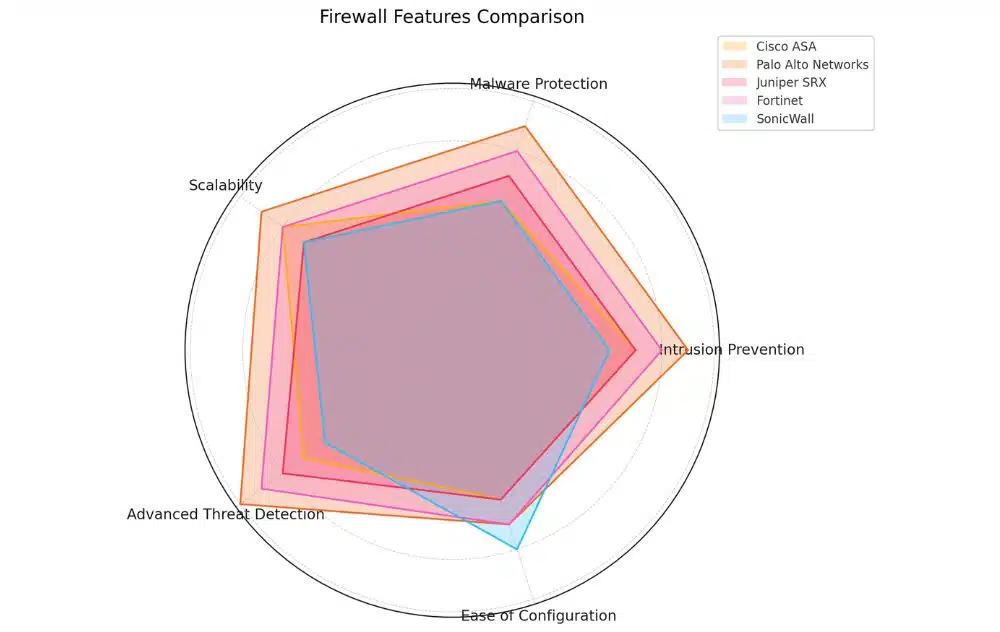
Comparison of Popular Firewall Solutions
Consider the following comparison of popular firewall solutions:
| Firewall Solution | Key Features |
|---|---|
| Cisco ASA | High-performance, scalable, and secure |
| Juniper SRX | Integrated threat intelligence, advanced security features |
| Palo Alto Networks | Application-aware, scalable, and secure |
In fact, each of these solutions has its strengths and weaknesses, and the right choice for you will depend on your specific needs and requirements.
Total Cost of Ownership (TCO) Considerations
Firewall costs extend beyond the initial purchase price; you need to consider the total cost of ownership, including the cost of maintenance, upgrades, and support can add up quickly.
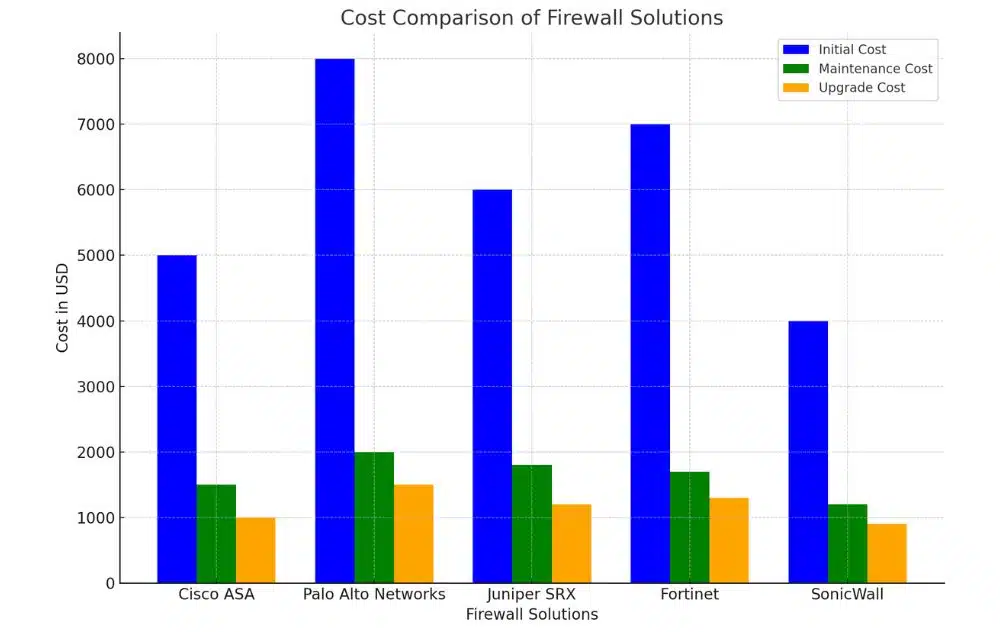
The TCO includes hardware and software costs, as well as the cost of personnel, training, and maintenance. You need to evaluate these costs carefully to ensure that your chosen firewall solution fits within your budget.
The cost of ownership will vary depending on the complexity of your network, the size of your organization, and the level of security required. Be sure to factor in the cost of potential security breaches and downtime when evaluating the TCO.
Legal and Compliance Aspects
Not only do firewalls play a vital role in protecting your network from cyber threats, but they also have significant legal and compliance implications.
Regulatory Requirements Related to Firewalls
Among the various regulations governing network security, some specifically address firewalls. For instance, the Federal Information Security Management Act (FISMA) requires federal agencies to implement firewalls to protect their information systems. Similarly, the Gramm-Leach-Bliley Act (GLBA) mandates financial institutions to have firewalls in place to safeguard customer data.
Data Protection and Privacy Considerations
Across various industries, organizations are obligated to protect sensitive data and maintain privacy. Firewalls are important in this regard, as they help prevent unauthorized access to confidential information.
With the increasing importance of data protection and privacy, you must ensure that your firewall configuration aligns with relevant regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). This includes implementing measures to detect and respond to data breaches, as well as ensuring that your firewall rules are regularly reviewed and updated.
Industry-Specific Compliance (e.g., PCI DSS, HIPAA)
The Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA) are examples of industry-specific regulations that require organizations to implement firewalls to protect sensitive data it is important to consult with a qualified security expert to ensure compliance with these regulations.
Regulatory bodies governing these industries provide detailed guidelines for firewall implementation, configuration, and maintenance. You must familiarize yourself with these requirements to ensure that your firewall setup meets the necessary standards failure to comply can result in severe penalties and reputational damage.
Summing up
Upon reflecting on what you’ve learned from “Firewalls Demystified: A Comprehensive Guide to Network Security“, you now possess a solid understanding of the fundamental concepts and best practices surrounding firewalls and network security. You’ve gained insight into the technical aspects of firewalls, as well as practical advice on how to implement and maintain a secure network infrastructure. With this newfound knowledge, you’re better equipped to protect your digital assets from potential threats and make informed decisions about your organization’s network security strategy.



